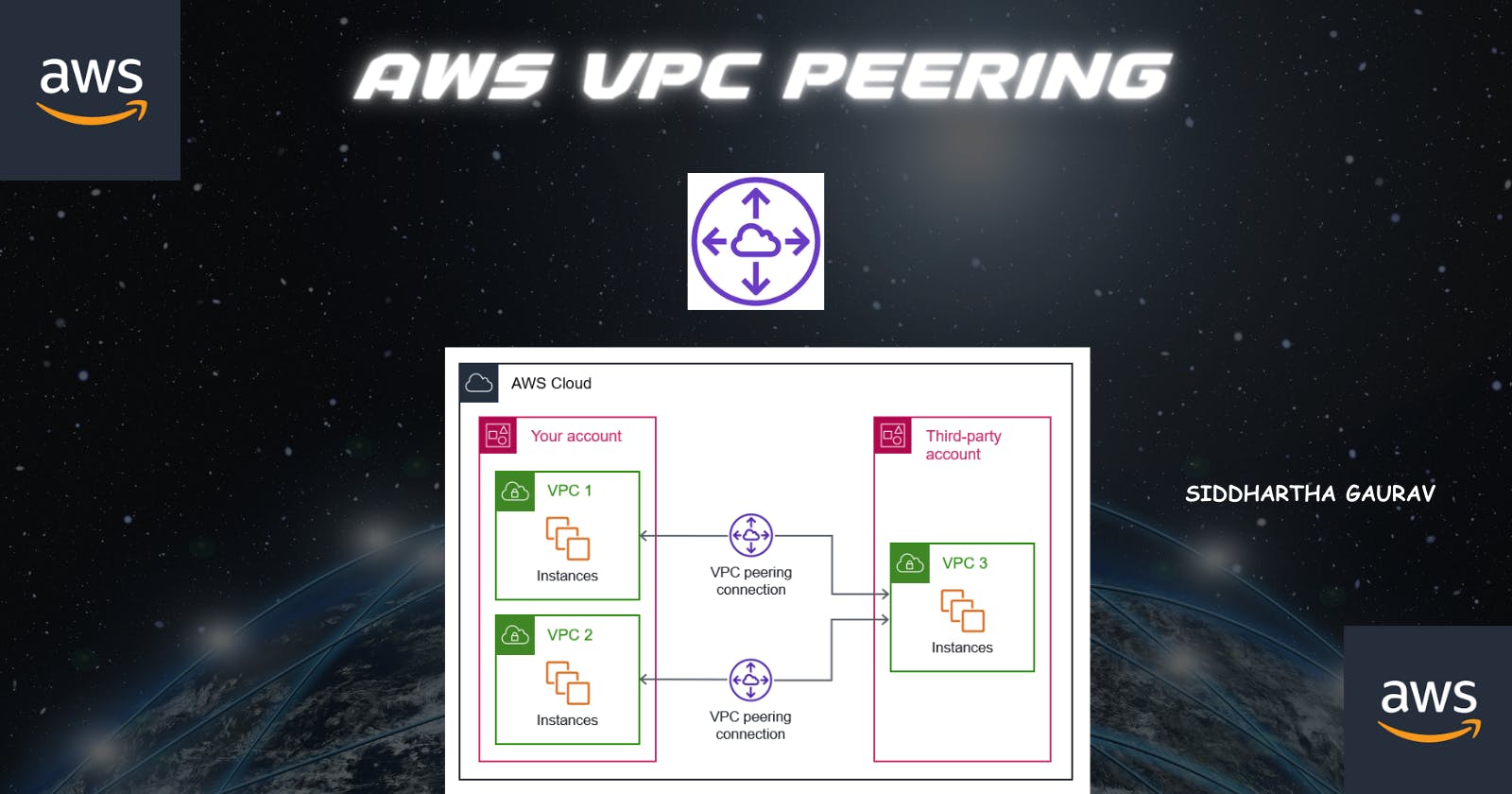
Amazon Web Services (AWS) offers a robust networking service called Virtual Private Cloud (VPC) that allows users to create a logically isolated section of the AWS Cloud where they can launch resources. VPC Peering is a powerful feature within AWS that enables seamless communication between VPCs, creating a virtual network that spans multiple AWS accounts.
What is AWS VPC Peering?
VPC Peering is a networking connection between two VPCs that allows them to communicate with each other as if they were in the same network. This connection is established by using private IP addresses, which means that the traffic between the VPCs stays within the AWS network and doesn't traverse the public internet.
Key Concepts
Sender and Receiver VPCs
In a VPC Peering connection, there are two VPCs involved: the sender (initiating the peering request) and the receiver (accepting the peering request). Both VPCs can belong to the same AWS account or different AWS accounts.
CIDR Blocks
CIDR (Classless Inter-Domain Routing) blocks are used to define the IP address ranges of the VPCs involved in the peering connection. It's crucial to ensure that the CIDR blocks do not overlap, as overlapping CIDR blocks would lead to routing conflicts.
Lab on VPC Peering
In the below lab, we are going to perform below operations -
Create one VPC in Mumbai and one in Ohio. These two are isolated from each other as there are two different VPC.
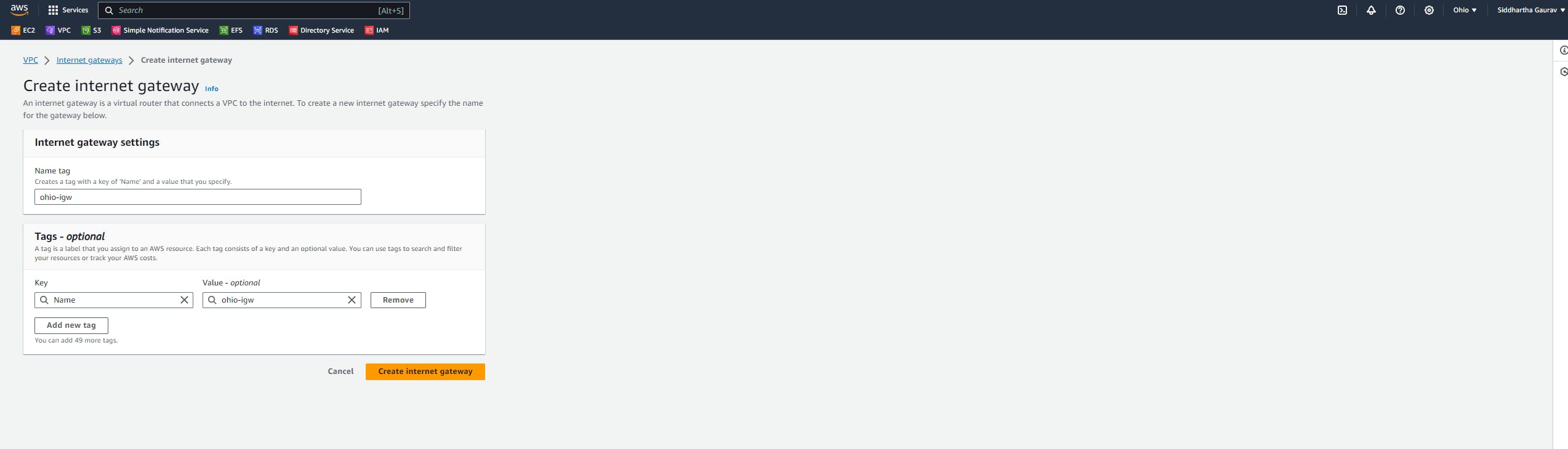
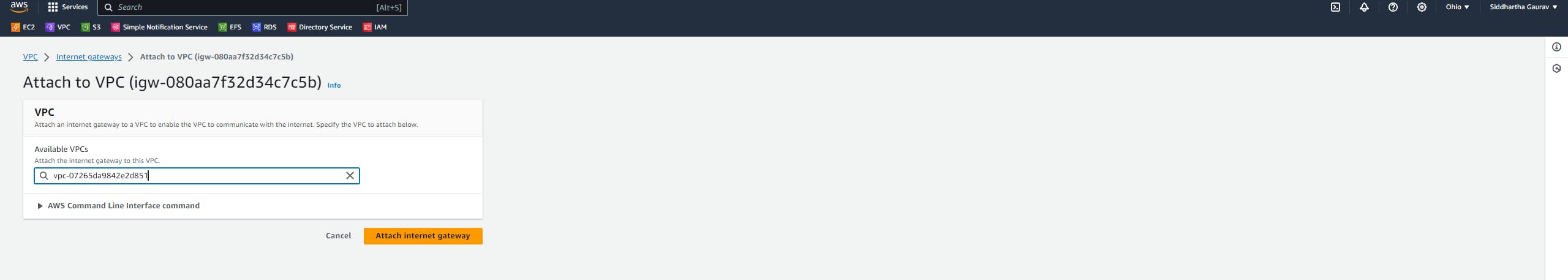
As a part of VPC creation, create subnets, an Internet gateway and attach this internet gateway to the new VPC, create a custom route table and associate your subnets, and add your routes for the internet.
We are picking below values for our lab -
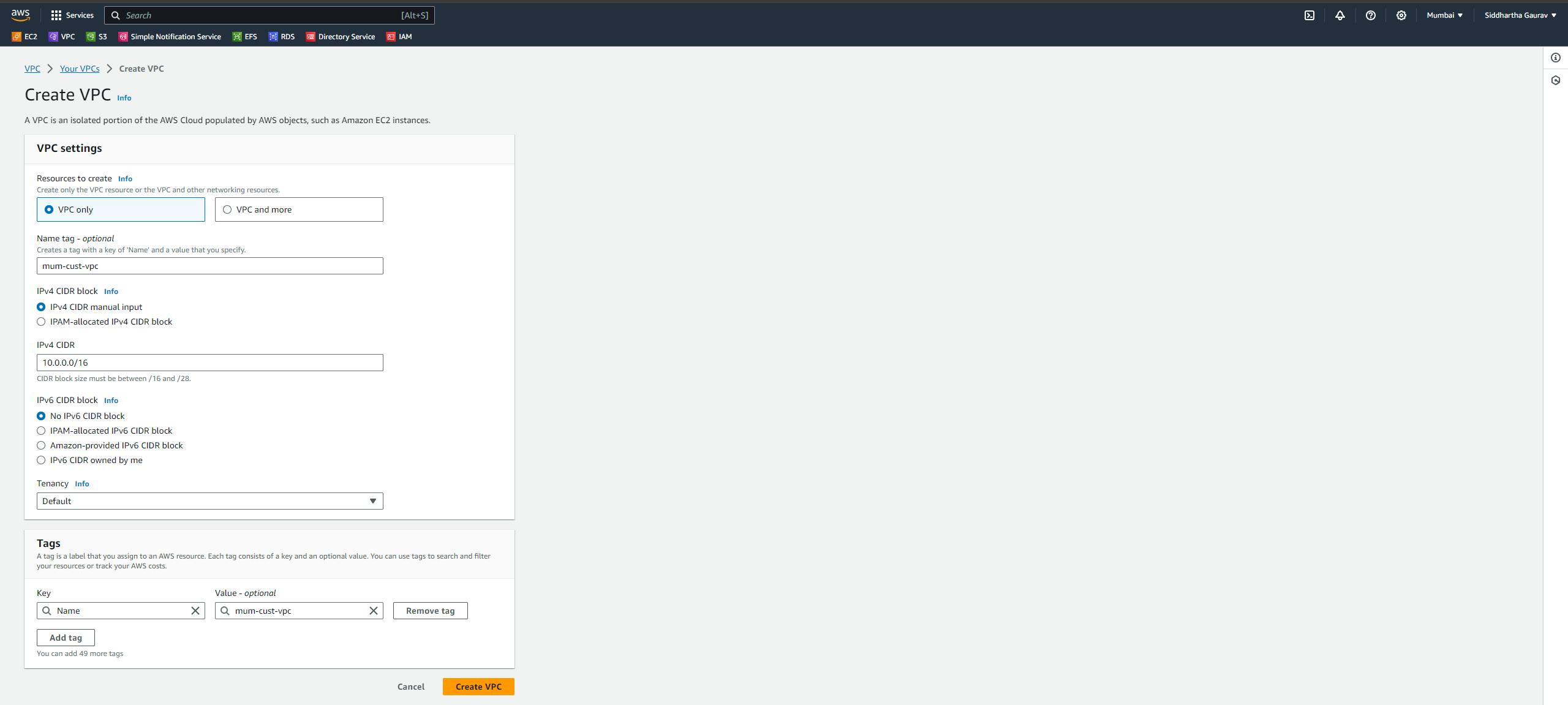
Mumbai VPC CIDR: 10.0.0.0/16
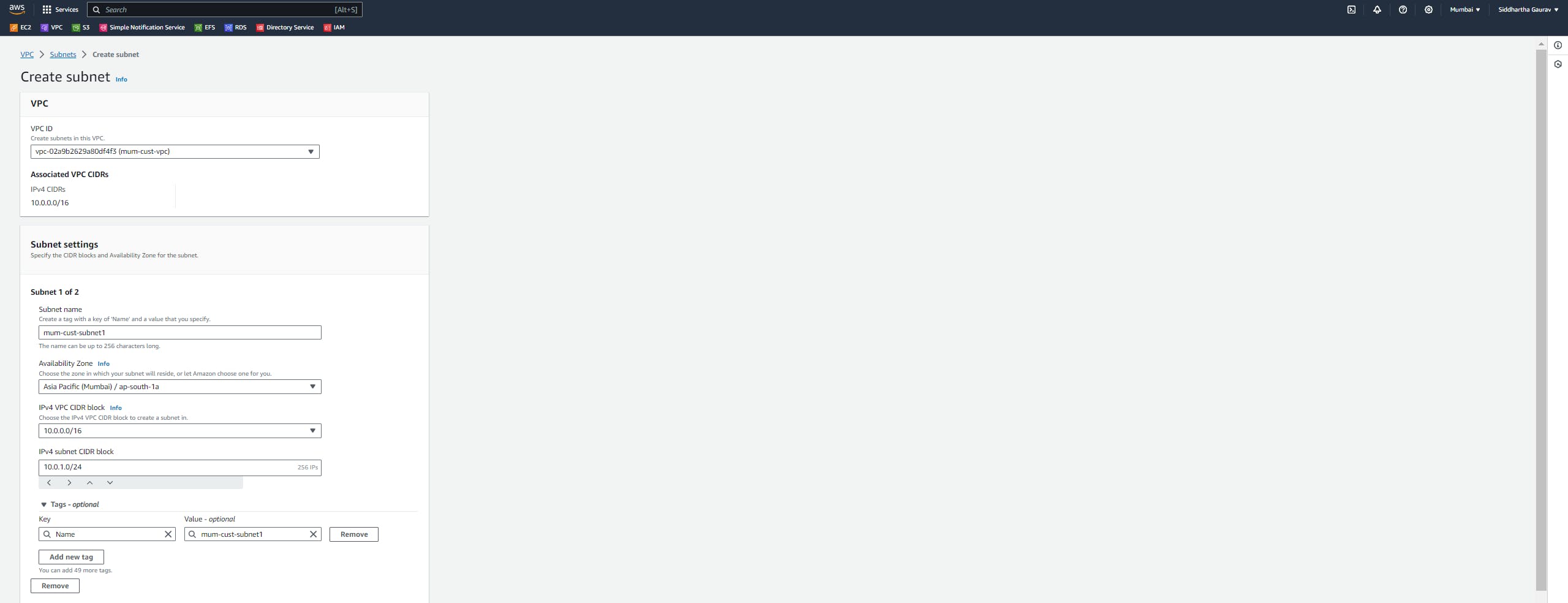
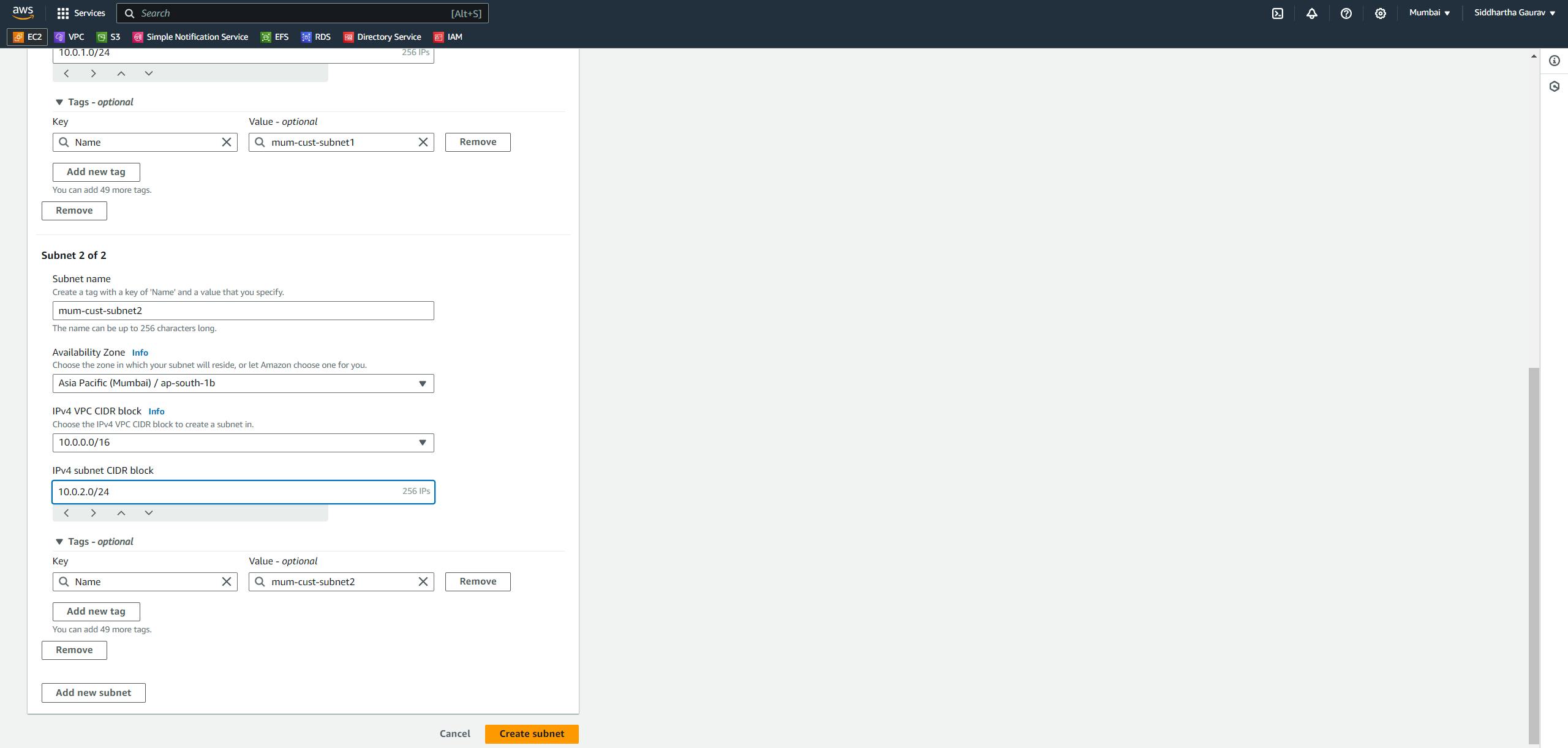
Mumbai Subnets: mum-cust-subnet1 - 10.0.1.0/24
mum-cust-subnet2 - 10.0.2.0/24
Ohio VPC CIDR: 172.16.0.0/16
Ohio Subnets: ohio-cust-subnet1 - 172.16.1.0/24
Take reference for creating a VPC from the blog - https://sgaurav.hashnode.dev/understanding-aws-vpc-a-beginners-guide
Create one EC2 instance on all the subnets, it means two in Mumbai VPC and one in Ohio VPC.
Once instances are ready, will first ping the EC2 instances in the same subnet and then ping them in two different VPCs.
- Below is the pictorial diagram of our lab -

Below are the above lab screenshots:
Task 1: Mumbai VPC Creation :






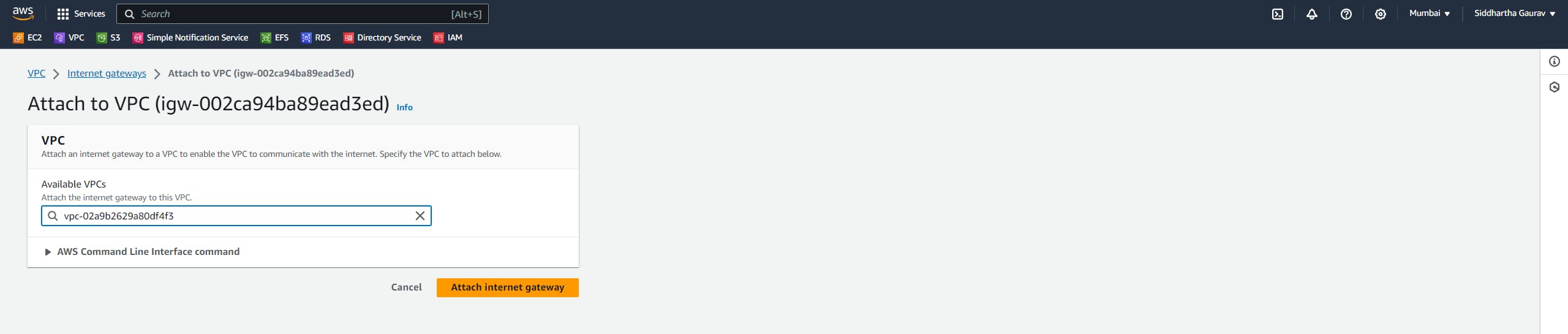


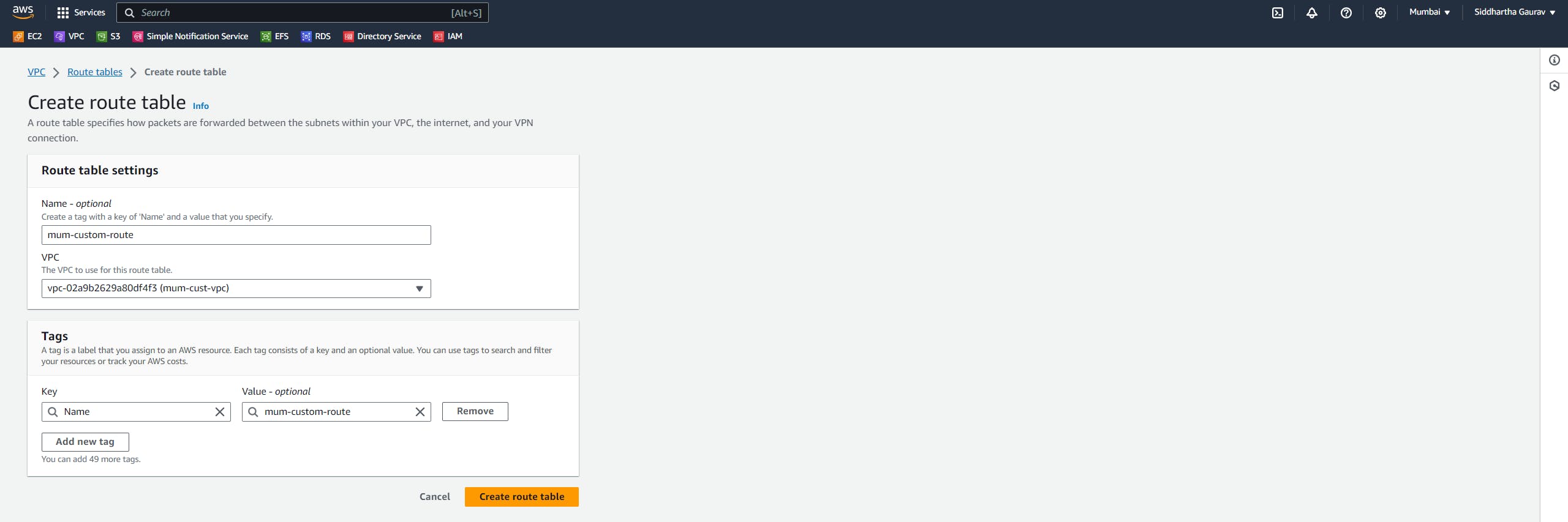


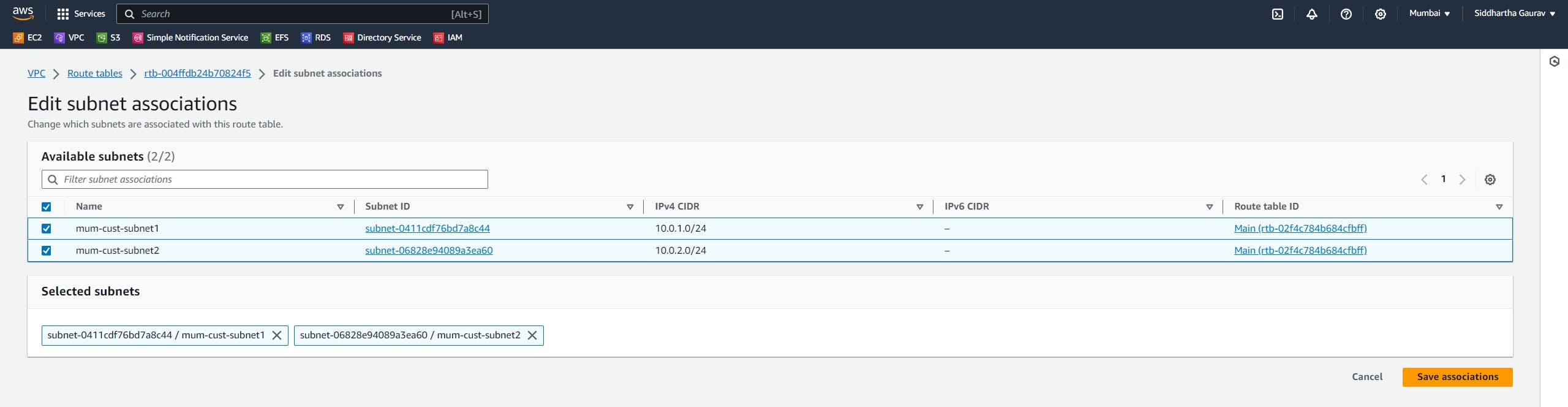
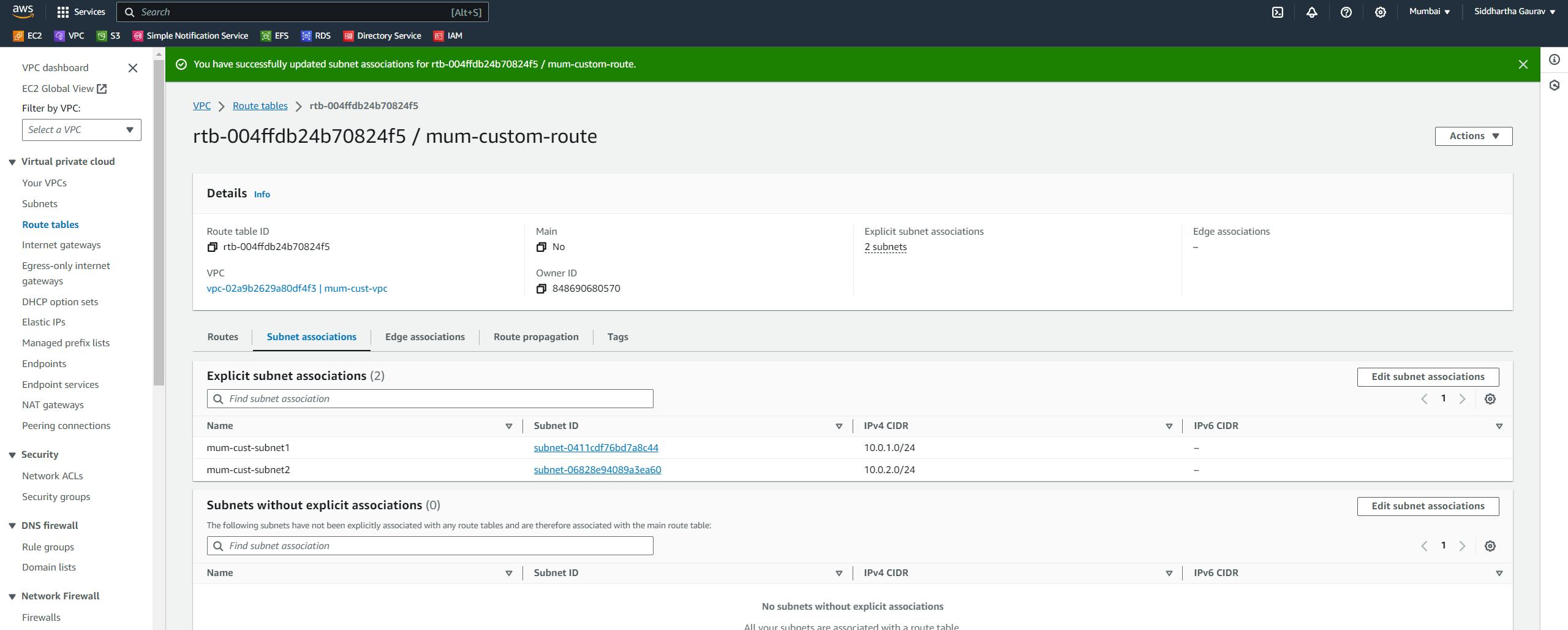
After this, launch one EC2 instance in both the subnets.

Let's ping both the EC2 instances from each other -


Hurray, our first test case is passed, bot the EC2 instances are reachable to each other.
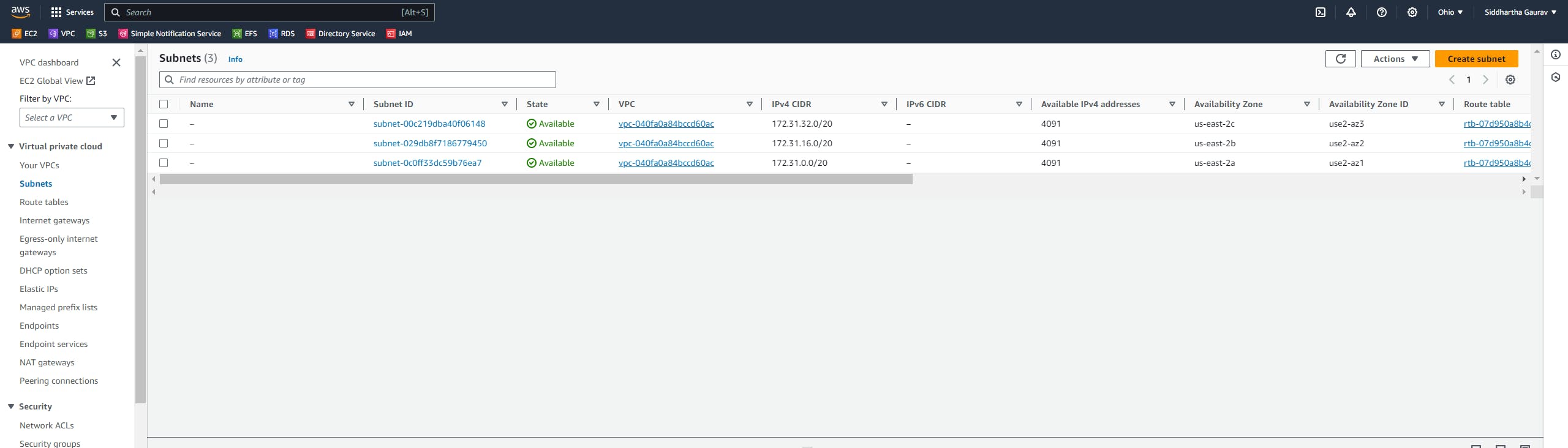
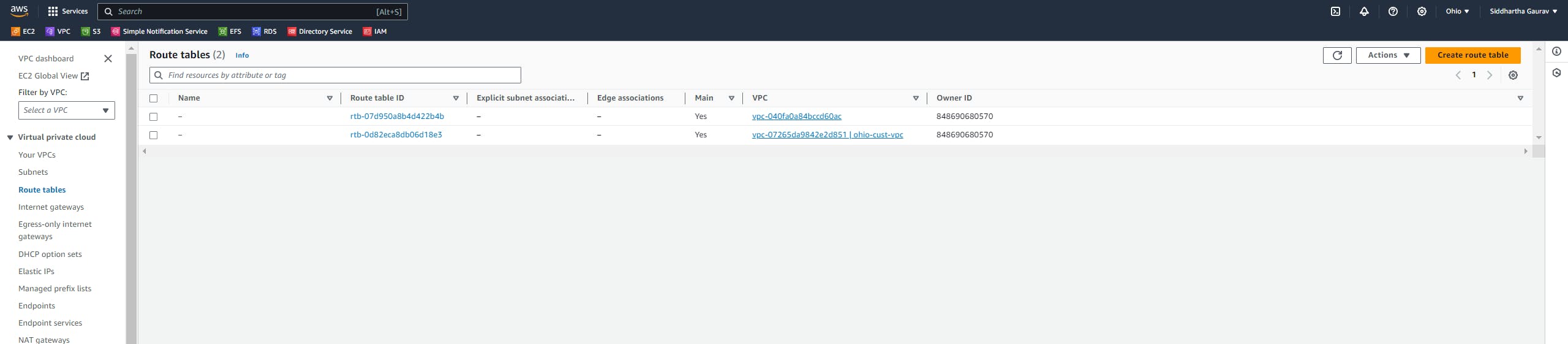
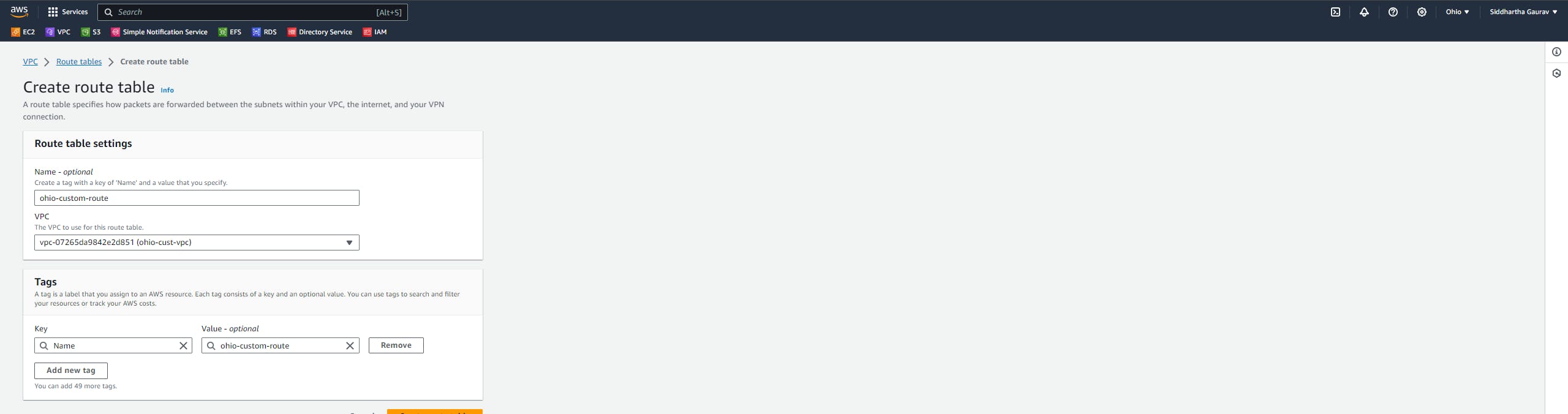
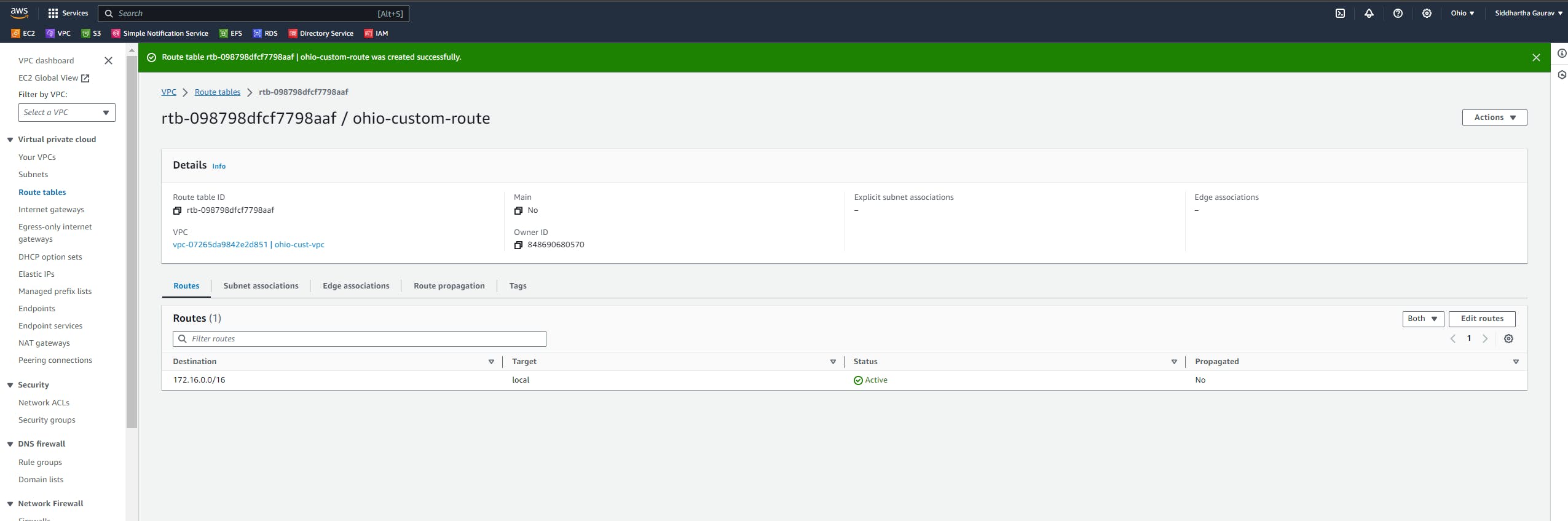
Similarly, create one VPC in the Ohio region and one subnet and all other stuff required for VPC.
Task 2 :Ohio VPC Creation :








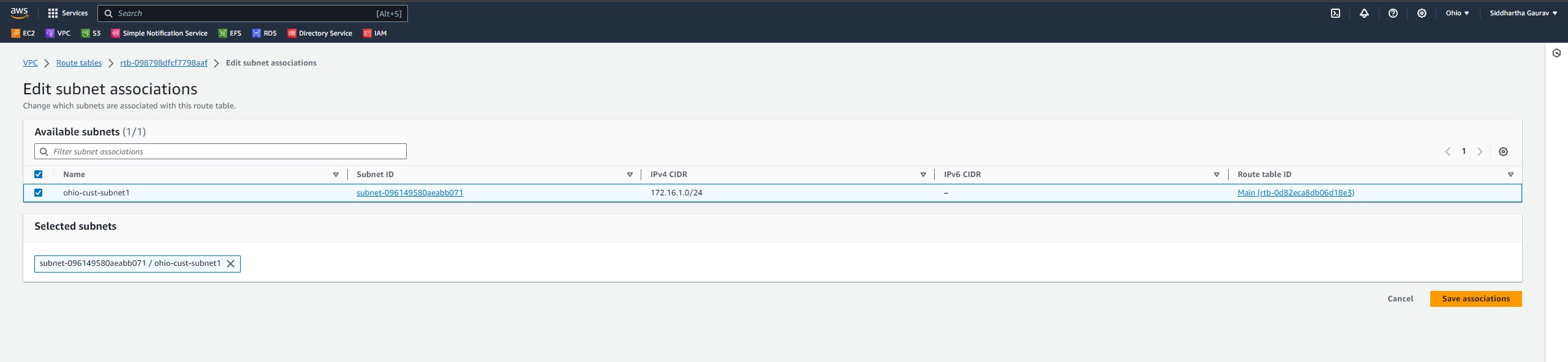

Launch one EC2 instance in this custom Ohio VPC.

Task 3 : Ping the EC2 machines from both Custom VPC
Let's first ping the Mumbai EC2 instance from Ohio EC2.
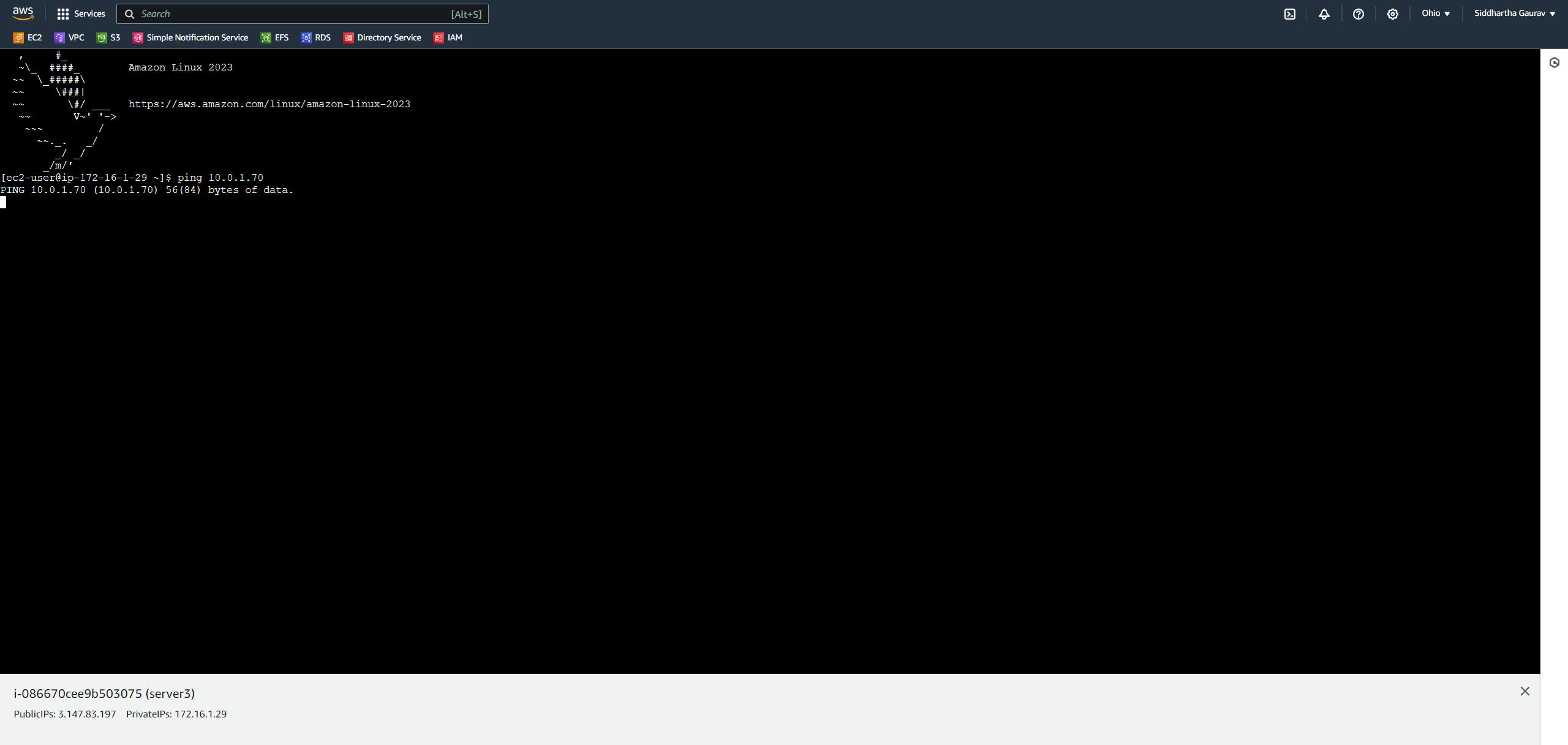
The Ohio EC2 instance is not pinging the Mumbai instance.
Let's check vice-versa.
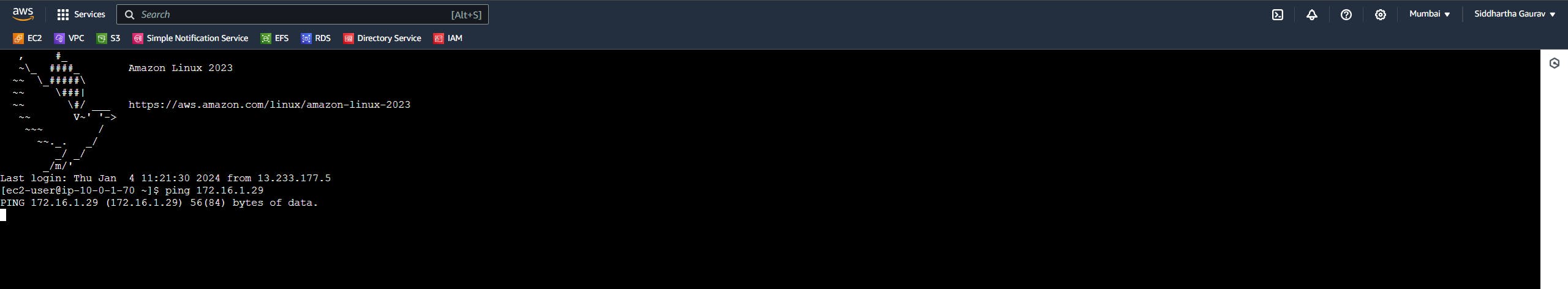
The Mumbai EC2 instance is also not pinging the Ohio instance.
To make this work, we need to do VPC peering.
Task 4 :How to Create VPC Peering
Initiate Peering Request:
In the AWS Management Console, navigate to the VPC dashboard.
Choose "Peering Connections" and click "Create Peering Connection."
Enter the account ID and VPC ID of the target VPC.
Let's create this request from Mumbai to Ohio. We don't need to enter account ID as we are doing in the same account.

Click on 'Create peering connection'.
Give the peering connection name and select your requestor VPC ID which is our custom Mumbai VPC ID.
In option 'Select another VPC to peer with', select my account and select the another region as we created in Ohio region.
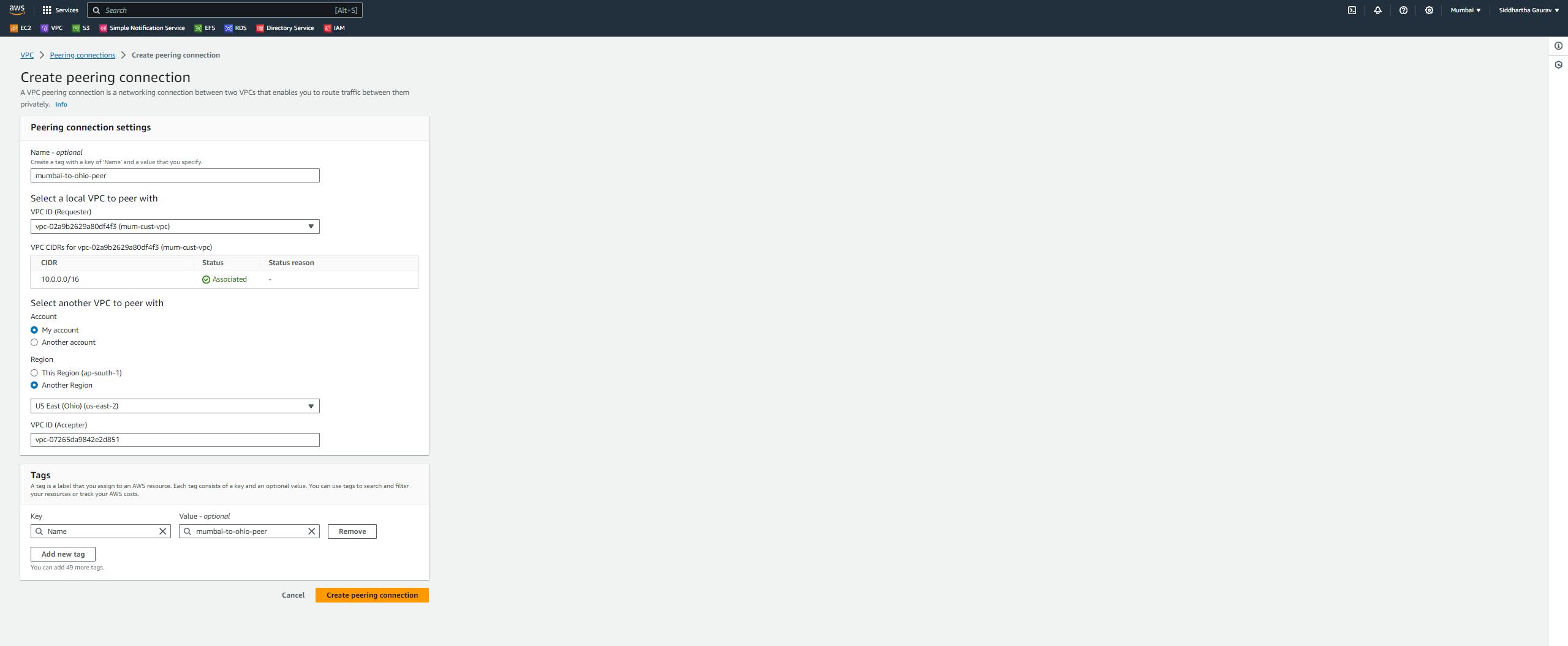
Click on 'Create peering connection'.
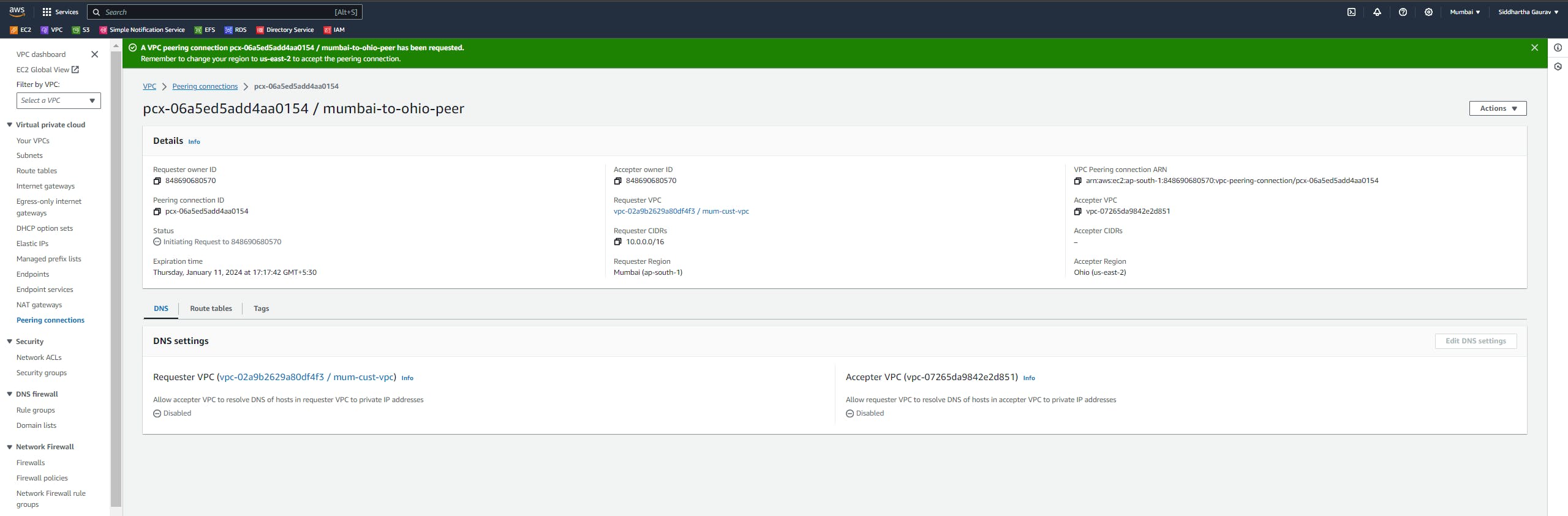
Accept Peering Request:
In the target VPC's AWS Management Console, navigate to "Peering Connections."
Select the peering connection request and accept it.
Go to the accepter Peering region which is Ohio in our case.
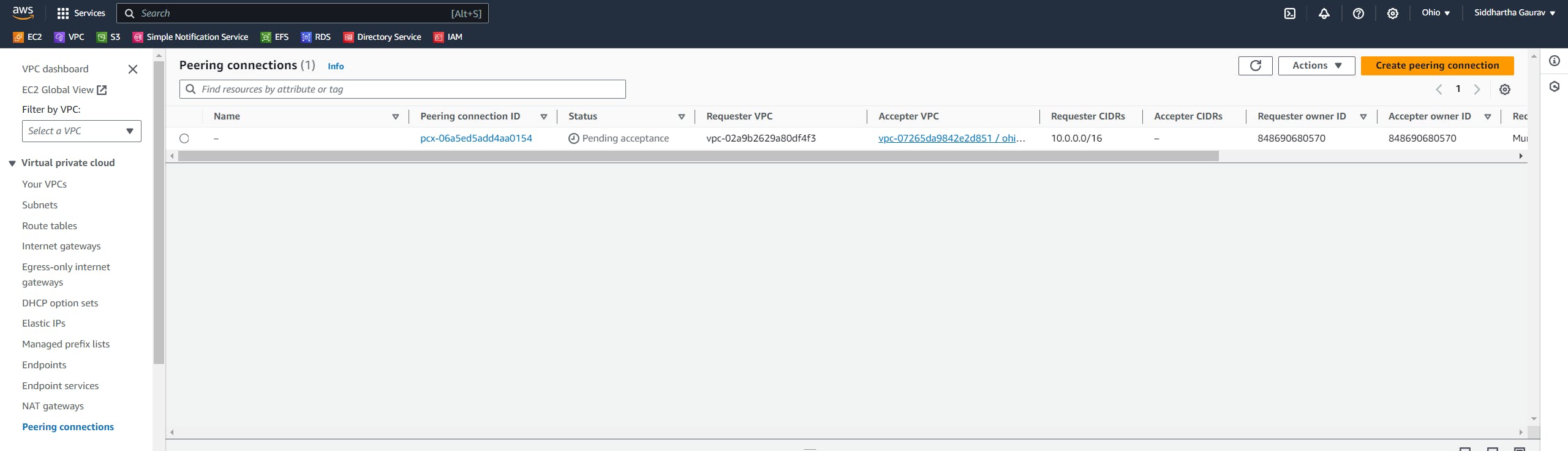
We can see above that we have one request pending for acceptance.
Select the request and click on 'Actions' -> 'Accept request'.
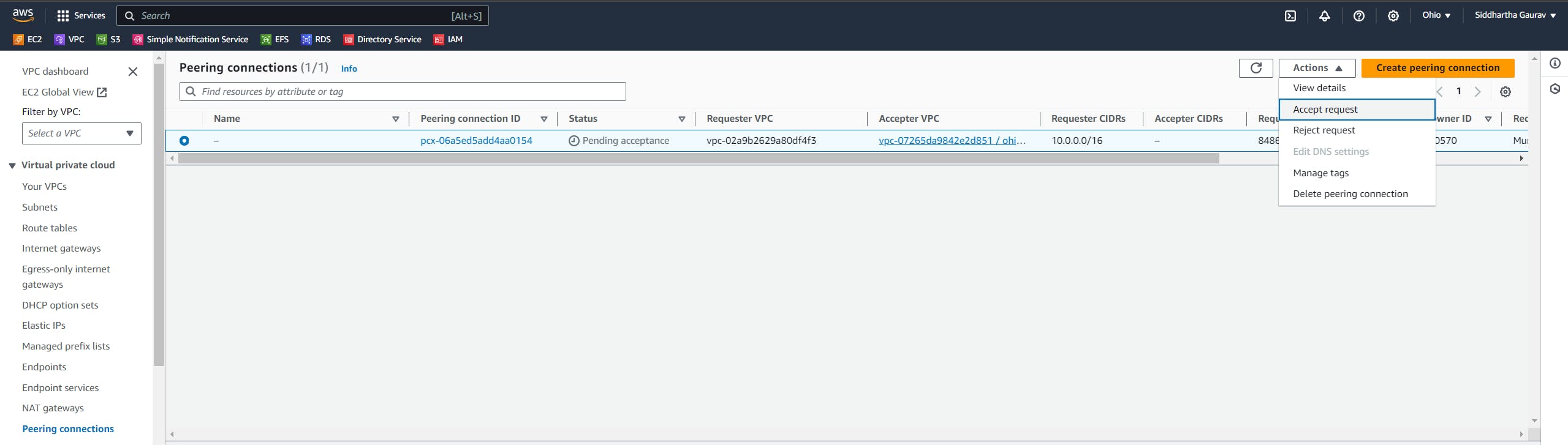

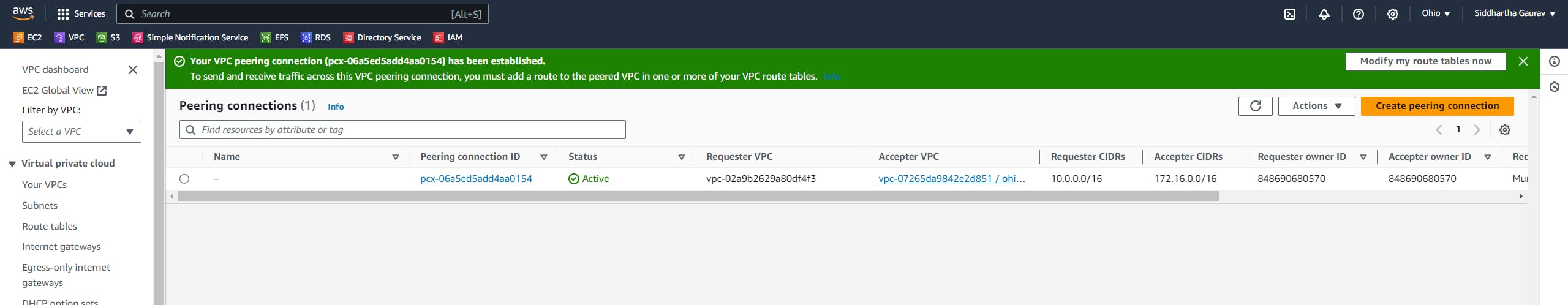
Our peering connections are now done.
Update Route Tables:
- Update the route tables in both VPCs to include routes for the CIDR block of the other VPC.
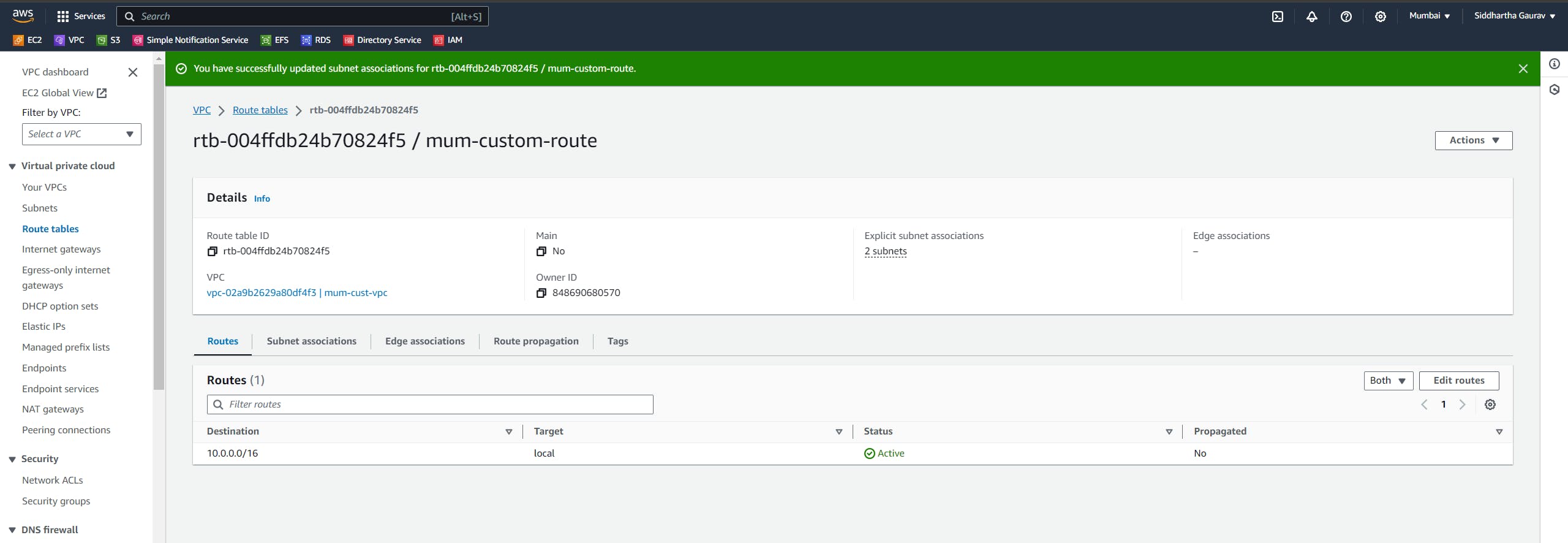
Let's first update the Mumbai custom route table :
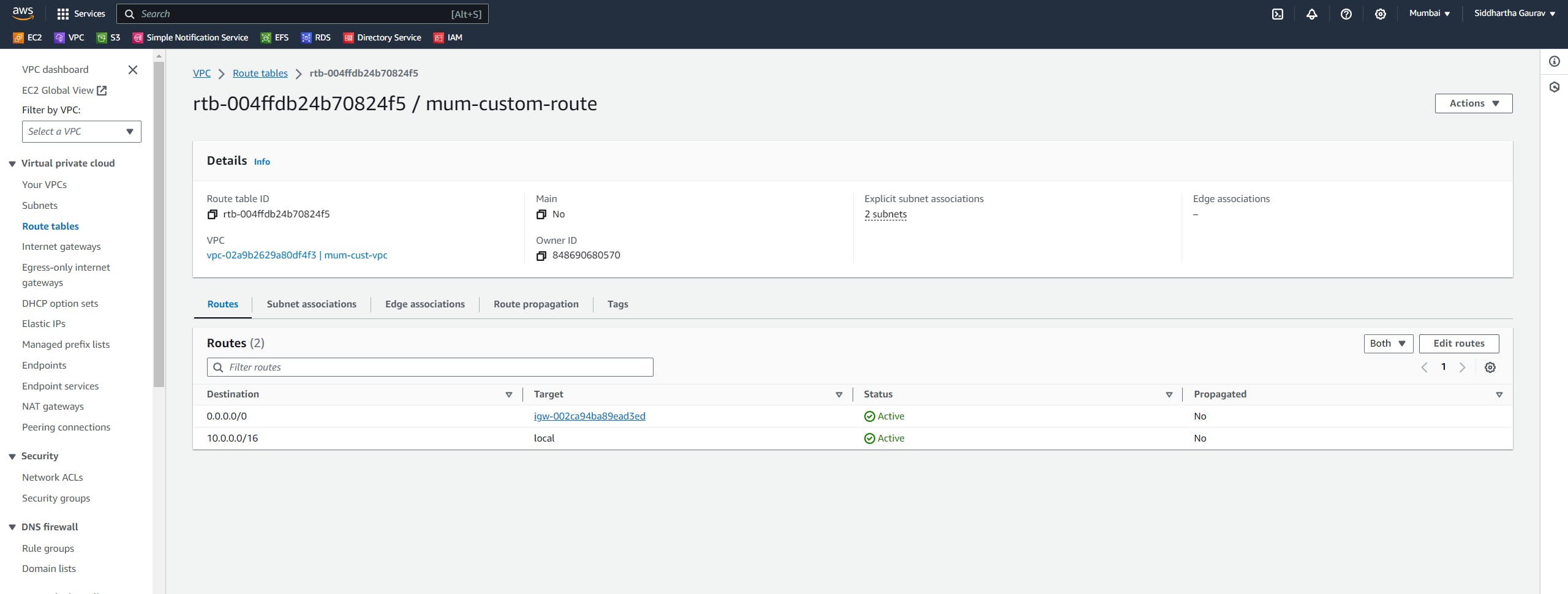
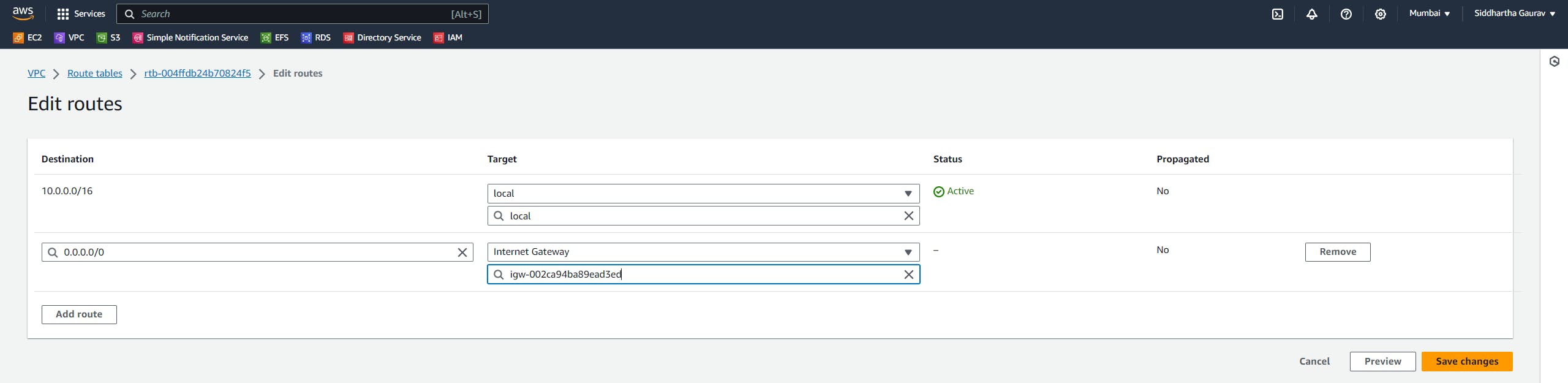
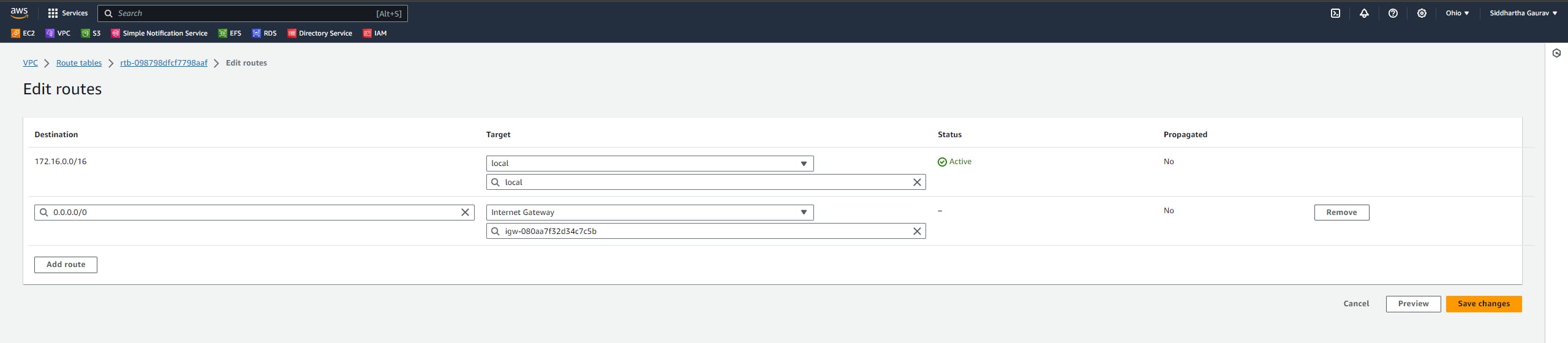
Click on 'Edit routes'.
Give the Ohio custom VPC CIDR as destination and target is our newly created peering connection.

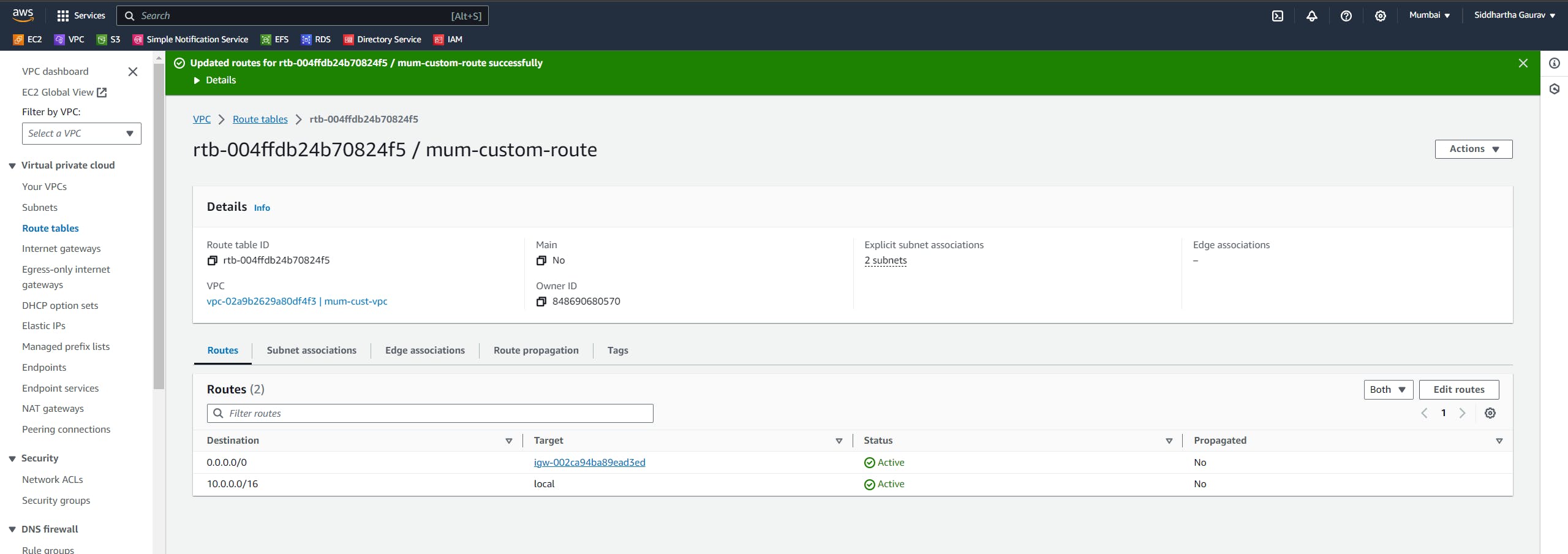
Save the changes.
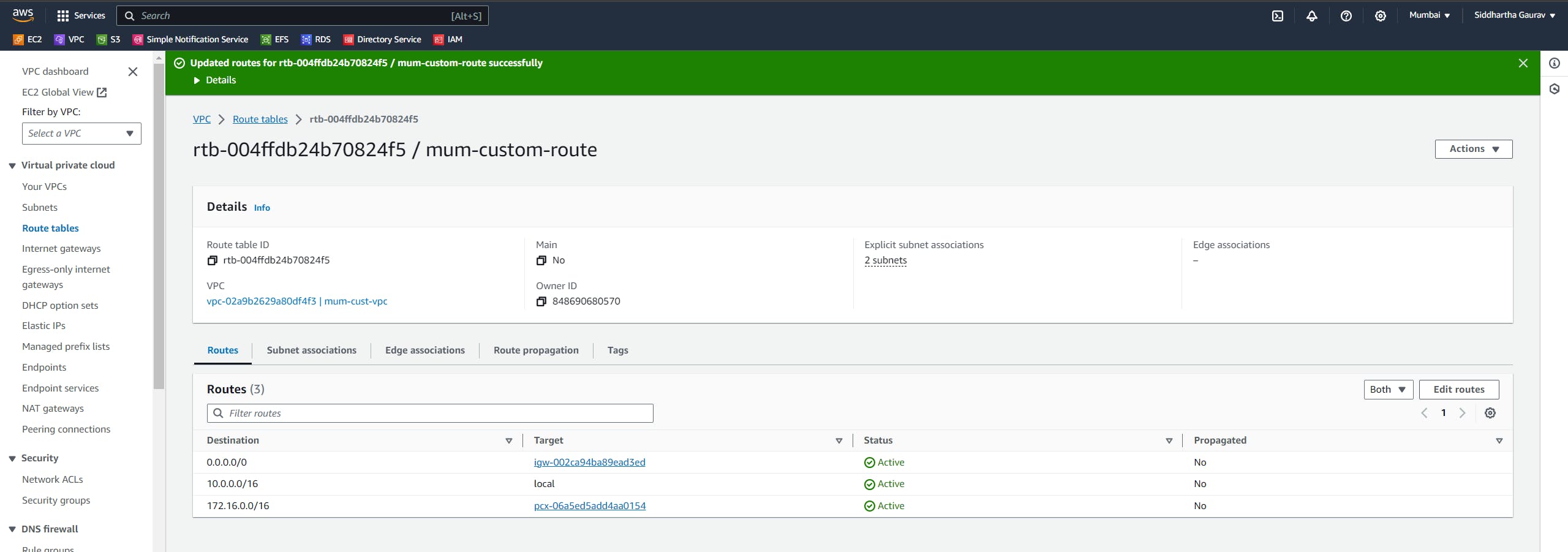
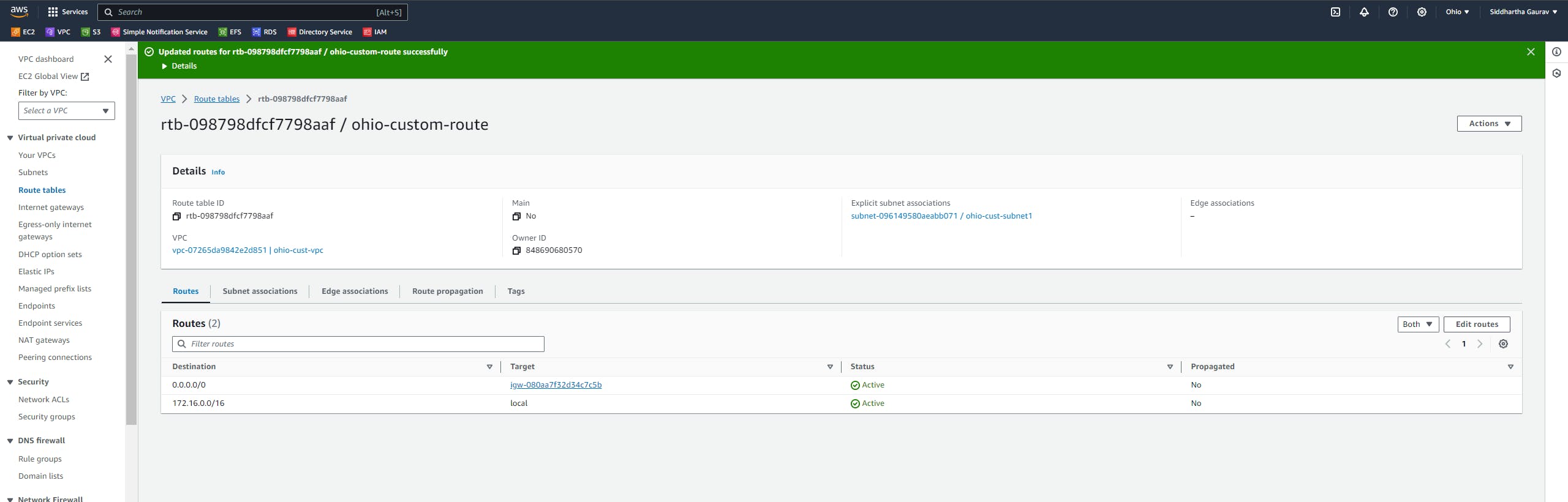
Now, do the same thing in Ohio custom route table.

Click on 'Edit routes'.
Give the Mumbai custom VPC CIDR as the destination and the target is our newly created peering connection.
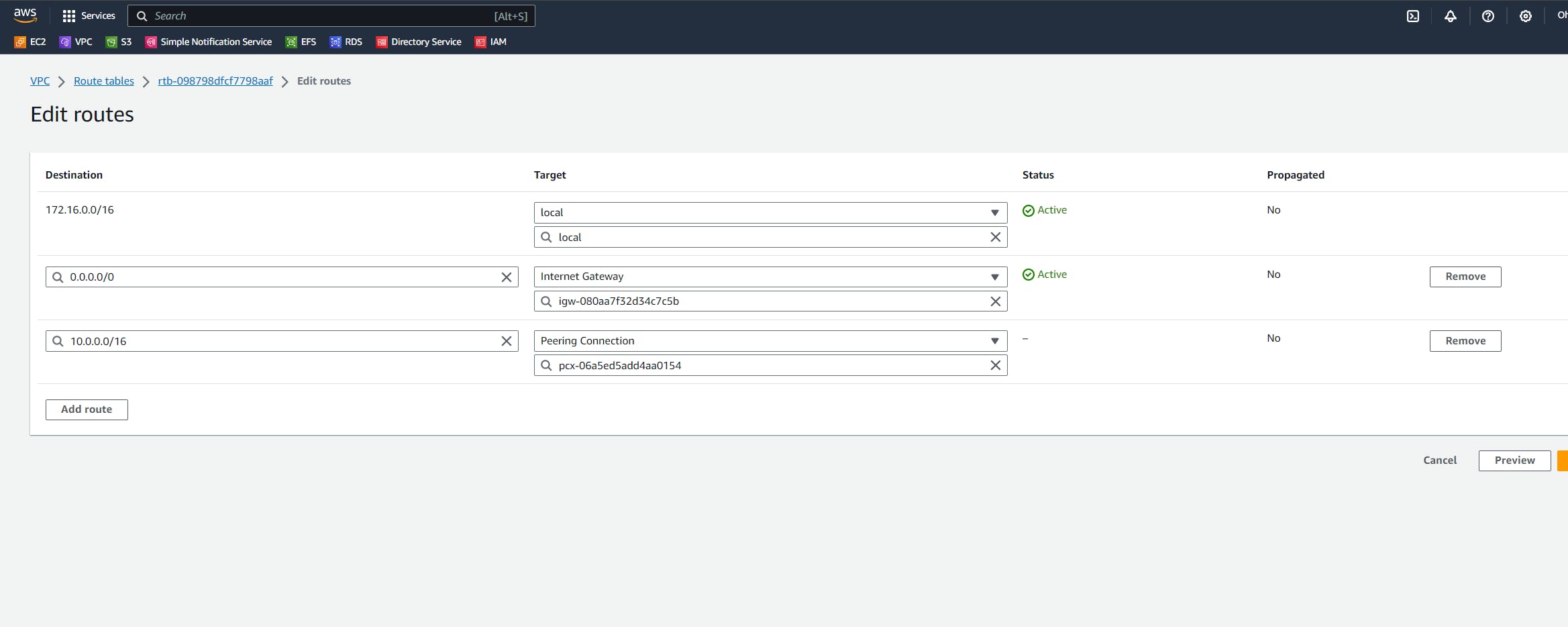
Save the changes.

Finally, all of our tasks are now done. 😊😊
Testing Connectivity:
- Once the peering connection is established, test connectivity between resources in the peered VPCs.
First test ping from Ohio EC2 to Mumbai EC2 :
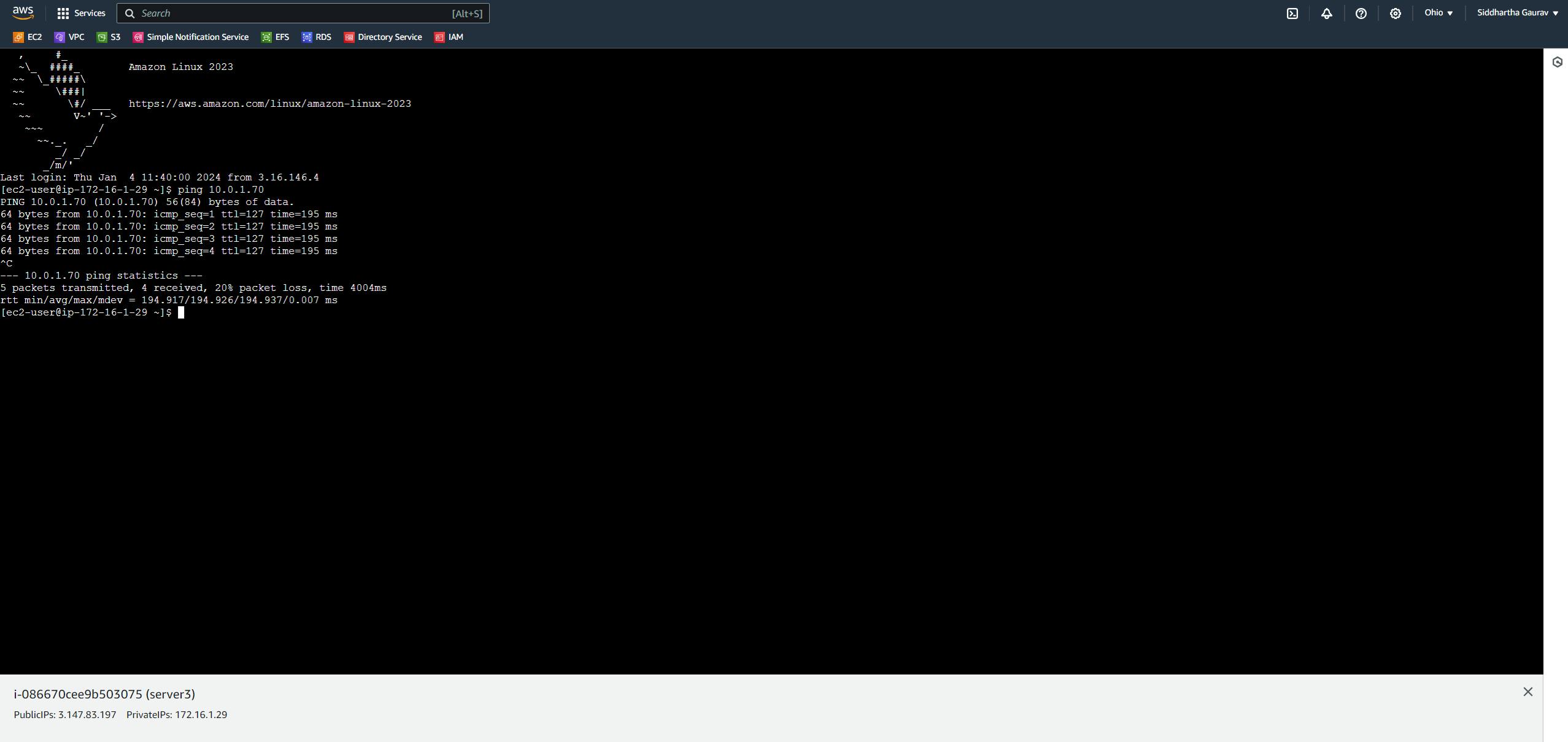
Hurray!! our Ohio EC2 instance can reach the Mumbai EC2 and both are running in isolated VPC.can
Now ping from Mumbai EC2 to Ohio EC2 :
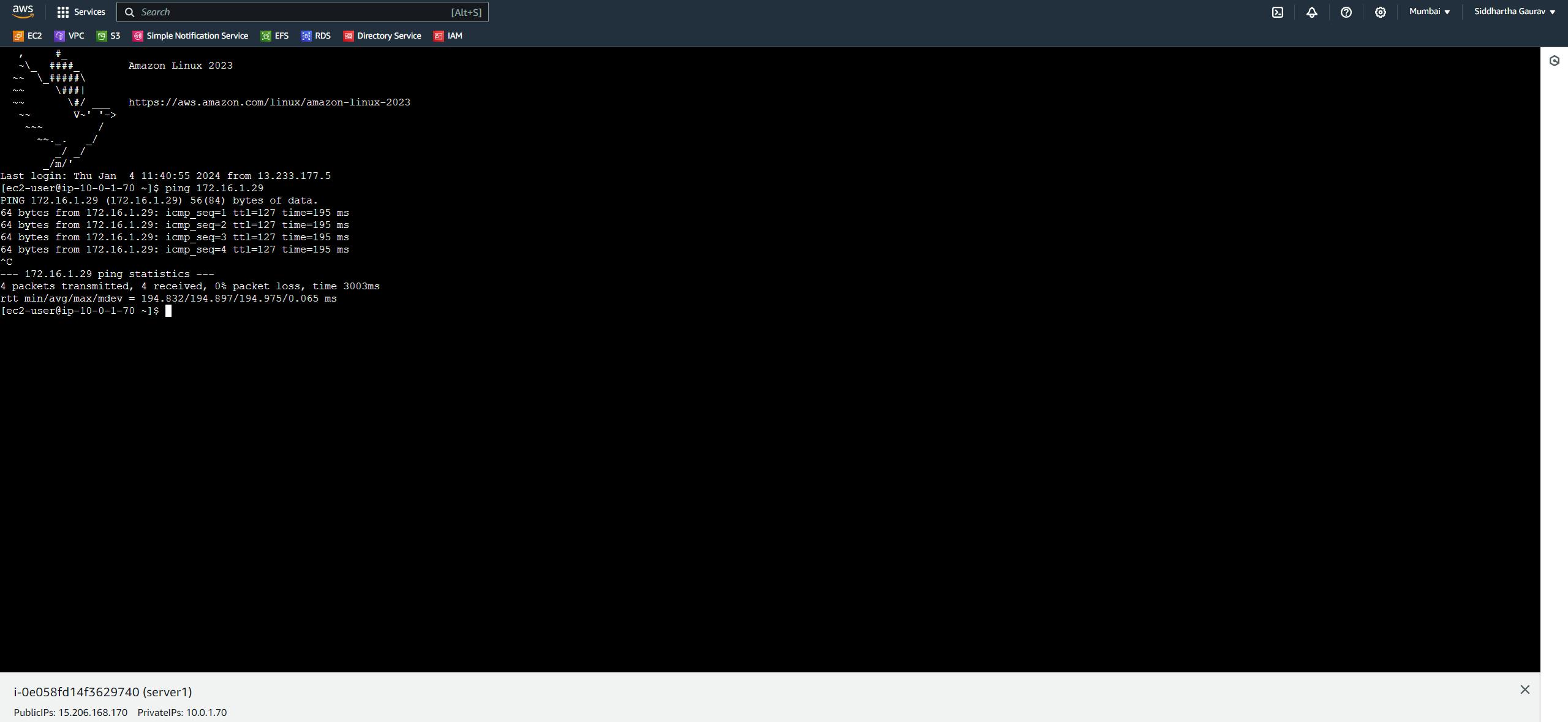
Vice-versa is also working fine. 😊😊
Considerations and Best Practices
Transitive Peering: VPC peering is not transitive, meaning if VPC A is peered with VPC B and VPC B is peered with VPC C, there is no direct connectivity between VPCs A and C. Separate peering connections are required.
Security Groups and Network ACLs: Ensure that security groups and network ACLs are appropriately configured to allow the necessary traffic between peered VPCs.
Data Transfer Costs: While data transfer between peered VPCs in the same region is free, there may be data transfer costs for inter-region peering.
Conclusion
AWS VPC Peering simplifies network communication between VPCs, offering a secure and scalable solution for connecting resources across different accounts or within the same account. By understanding the basic concepts and following best practices, beginners can leverage VPC Peering to build flexible and efficient multi-VPC architectures on AWS.
Start exploring the capabilities of AWS VPC Peering to enhance the connectivity and collaboration of your cloud resources!